Why 264.68.111.161 is not a valid IPv4 address
IP addresses are fundamental to internet communication, routing, and identification. Every internet-connected device uses an IP address to function correctly. Among the many addresses seen or referenced, 264.68.111.161 is one that raises immediate red flags for network engineers and digital infrastructure professionals. This article explores its nature, structure, usage misconceptions, and what it reveals about network misconfiguration or invalid addressing practices.
Understanding the Structure of IPv4
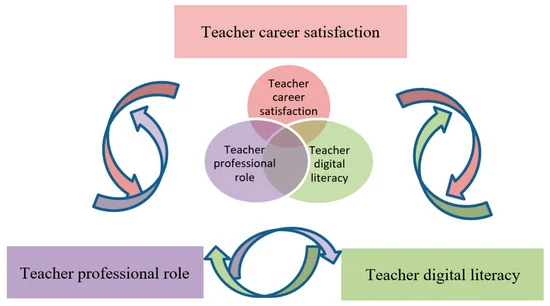
An IPv4 address consists of four octets. Each octet is separated by a dot and ranges from zero to two hundred fifty five. This format allows about four billion unique address combinations. The structure is governed by standards that ensure proper routing and communication between systems. Any value outside this predefined range is immediately flagged as invalid.
In the address 264.68.111.161, the first octet 264 exceeds the valid range. Therefore, 264.68.111.161 does not represent a valid IPv4 address.
Why 264.68.111.161 Is Not Valid
The first number in an IPv4 address must not go beyond 255. Because 264 is greater than the upper limit, the address is syntactically invalid and will not function within any operating system, network router, or internet protocol stack.
This form of error is often caused by one of the following:
-
Manual entry mistakes
-
Misconfigured network scripts
-
Use in placeholder IPs in examples or pseudo logs
-
Ignorance of the IPv4 range restrictions
IPv4 segments must remain within 0 to 255
Common Contexts Where Invalid IPs Appear
Server Logs and Debugging:
Invalid IPs such as this may appear during application logging or testing scenarios where real addresses are not yet assigned.
Malware and Phishing Bait:
Some malicious payloads or botnets use invalid IPs to evade firewall and IDS systems.
Educational Content:
Tutorials may use invalid IPs intentionally to explain addressing constraints or validation.
Network Diagnostic Errors:
When an internal system is not correctly assigning addresses, such out-of-range IPs may accidentally be generated.
How Operating Systems Handle It
If someone attempts to assign 264.68.111.161 manually to a device, the operating system will reject it. Systems like Windows, Linux, and macOS have built-in validations that prevent such assignments. Tools like ipconfig or ifconfig would return an error or simply ignore the input.
Routers and Network Equipment Response
Routers, firewalls, and modems do not accept invalid IP addresses like 264.68.111.161. They are built to drop or discard such packets. Network address translation (NAT), routing tables, and DHCP services require strict compliance with IP syntax rules.
Misleading Appearances in Network Tools
Certain tools may still show such IP addresses when configured improperly or when data is simulated. Security logs, honeypot systems, or misconfigured logging software may list these types of addresses. However, they are never used for actual communication.
Security Implications
Though an invalid IP cannot be used for actual traffic, its presence in logs or error reports may indicate:
-
Spoofed input
-
Vulnerable scripts
-
Misconfigured services
-
Attempts to bypass validation
Security analysts often review such logs to determine if malformed data is being introduced deliberately as part of an attack strategy.
How to Fix and Validate
To correct the error:
-
Replace the invalid octet with a valid one, such as changing 264 to 192
-
Use an IP validation tool
-
Verify address ranges against official documentation
-
Ensure DHCP servers are properly configured to assign valid ranges
System rejecting invalid IP address input
Valid Alternatives to 264.68.111.161
Instead of using an invalid IP, the following would be accepted:
-
192.68.111.161
-
10.68.111.161 (Private IP)
-
172.16.68.111 (Private IP)
-
203.0.113.161 (Reserved for documentation)
Why Accuracy in IP Addressing Matters
Incorrect IP configurations cause:
-
Network disconnections
-
Device communication failures
-
Increased troubleshooting time
-
Compromised security posture
Professional IT environments rely on strict validation for addressing, especially when configuring DNS, DHCP, VPNs, and static routes.
Final Thoughts
264.68.111.161, while formatted like an IPv4 address, is technically invalid. Its presence may signal test data, logging errors, or potential misconfigurations. By understanding how IP address validation works, users and administrators can avoid many common network issues.
To explore more topics related to network configuration, IP ranges, and addressing guides, visit Magazines Break.
Frequently Asked Questions
What is 264.68.111.161?
It appears like an IPv4 address but is invalid due to the first segment exceeding 255.
Why is 264.68.111.161 not a valid IP address?
IPv4 requires each segment to be between 0 and 255. The segment 264 violates this rule.
Can I use 264.68.111.161 in my router or server?
No. Most modern systems reject such addresses and prompt an error.
What happens if I see this in logs?
It may indicate misconfiguration, placeholder data, or spoofing attempts.
How do I validate a correct IP address?
Use tools like IP calculators or refer to IPv4 structure guidelines.
Can this address harm my system?
While invalid, its presence may point to deeper configuration or security issues.
Are addresses like 264.68.111.161 common?
They occur in simulated or incorrect setups, not in real production environments.
Is this an IPv6 format?
No. IPv6 uses colons and hexadecimal, not decimal with dots.
Why might someone use this address anyway?
As an example in documentation or intentionally for testing rejection logic.
What is the correct form for private IP addressing?
Use ranges such as 192.168.x.x, 10.x.x.x, or 172.16.x.x to 172.31.x.x.