
Example interface of an iofbodies.com application used for testing
iofbodies.com applications
The term iofbodies.com applications refers to a niche set of digital tools, utilities, or scripts typically circulated within underground or technical communities. These applications are not available on official app marketplaces and often require advanced understanding of cybersecurity, development environments, or data testing frameworks.
Many users arrive at this term looking for ways to access, download, or understand how these applications function. Others search to verify their safety or discover whether they serve any legal or practical use.
What are iofbodies.com applications
Applications tied to iofbodies.com are not your standard productivity or social apps. They are specialized utilities, often referenced in cybersecurity forums, experimental dev communities, or digital subcultures that deal with anonymity, testing, or scraping. Most of these applications are standalone executables, scripts, or backend tools used for exploring software environments, emulating traffic, or parsing data.
They are often experimental, unregulated, and distributed privately. As such, caution is required for anyone looking to explore them.
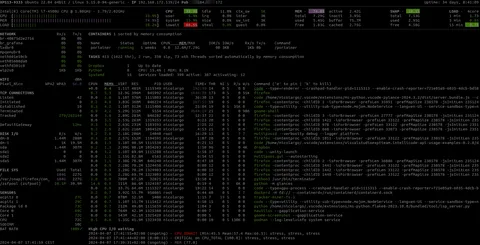
Where are iofbodies.com applications found
These applications are not indexed by search engines in the traditional sense. You will not find them on mainstream distribution platforms. They are typically accessed through private Telegram groups, anonymous file-sharing links, or encrypted message boards.
In many cases, the domain iofbodies.com serves as a landing page or placeholder for launching specific downloads or redirecting users to other encrypted sources. Tools are shared using temporary links or behind authentication layers that require invitation or credentials.
Are iofbodies.com applications safe
These applications carry significant risk if downloaded or installed without verification. The lack of transparency around their development, origin, and codebase means they may contain hidden scripts, backdoors, or data-stealing functions.
Experienced security researchers sometimes test them in virtual sandboxes to monitor behavior. General users, however, are strongly advised not to install them directly on personal or network-connected devices. The risks include unauthorized data access, device compromise, and exposure to legal liability if used improperly.
Use cases for iofbodies.com applications
Some people explore these tools for penetration testing, data scraping, spoofing, or emulation. Others use them to understand server behavior, simulate attacks for research, or test environments under non-standard conditions. Depending on the tool type, it might be capable of cloaking network identities, bypassing geolocation filters, or triggering API overload simulations.
While some of these use cases have legitimate research value, they can also be misused. This is why access to these tools is often gated and intentionally kept obscure.
How to interact with iofbodies.com applications safely
If you must explore these tools, do so only in secure environments. Use virtual machines disconnected from your main network. Scan all downloads through behavioral analysis tools like Cuckoo Sandbox. Use a dedicated VPN or isolated server stack. Never launch or install applications from this domain on a production system or a personal device.
Avoid interacting with any tool that does not come with source code or verifiable authorship. Tools that are open-source and audited are safer alternatives.
Community perception of iofbodies.com applications
Within online cybersecurity groups and penetration testing circles, there is a divided opinion on tools from iofbodies.com. Some users report success when testing server load simulations or web scraping structures. Others share warnings about persistent malware embedded within the application package.
Due to the lack of formal documentation, these tools often evolve through user discovery and shared knowledge. Discussions are active in hidden boards, archived forums, and encrypted chats where metadata is stripped to avoid traceability.
Legal status of iofbodies.com applications
Jurisdictions vary, but tools that can manipulate online services, scrape content without permission, or bypass authentication systems are often subject to legal limitations. Simply possessing such tools may not be illegal, but using them to interact with unauthorized services or data networks can be a breach of law in several countries.
Always review your local cybercrime regulations before engaging with any software that is not transparently documented or published under a known license.
Technical requirements for iofbodies.com applications
These applications usually require a non-standard runtime. Some work on command line interfaces, others use compiled code that depends on specific Linux distributions or kernel modules. Installing them often involves bypassing traditional installation protocols. That could mean altering root permissions, disabling antivirus layers, or using cracked shells.
This presents a serious concern. Inexperienced users can expose their system to irreversible changes, or worse, invite external control without ever noticing it.
Who uses iofbodies.com applications
Security professionals, penetration testers, and developers who specialize in digital forensics may study or test these applications under strict protocols. A majority of mainstream users who come across the keyword are often misled by rumors or misleading posts offering fake tools under the iofbodies.com label.
Tools from unknown or poorly documented sources should never be used on real infrastructure or sensitive systems.
Safer alternatives to iofbodies.com applications
There are legitimate open-source frameworks that offer similar technical capabilities. These include Kali Linux for penetration testing, Wireshark for traffic inspection, and Burp Suite for vulnerability testing. GitHub hosts many tools for ethical research that are fully documented, reviewed, and supported by active developer communities.
These tools provide transparency, regular updates, and safer integration paths for research or educational purposes.
Summary
iofbodies.com applications exist in a digital space that blends utility with risk. They attract attention from both curious users and technical experts due to their obscure presence and specialized function. While some tools may serve legitimate testing purposes, others pose real threats to device security, data privacy, and legal compliance.
Only experienced professionals with controlled environments should approach these applications. For most users, reputable and audited alternatives provide a much safer path.
For more insights into secure technology platforms and digital tool reviews, visit Magazines Break.
FAQs
What are iofbodies.com applications used for
These tools are used for digital testing, data parsing, and system emulation by advanced users and developers.
Are iofbodies.com applications safe to download
They are not considered safe for general users. Many contain harmful scripts or unverified code that may damage systems or compromise data.
Can iofbodies.com tools run on mobile devices
Most tools are made for Linux or PC environments. Only a few may work on rooted Android devices.
How do people access iofbodies.com applications
Access typically happens through invite-only links, hidden forums, or encrypted community channels. They are not available through public stores.
Are these tools legal to use
Depending on jurisdiction, some tools may violate cybercrime or data protection laws if used improperly or on unauthorized systems.
Do these applications require internet connection
Yes. Many applications interact with APIs, remote servers, or data streams and will not function offline.
What programming languages are used in these applications
Most tools use Python, Shell scripting, or C-based programming. Some are compiled for specific system architectures.
Who should use iofbodies.com applications
Only cybersecurity professionals or experienced developers should attempt to use or analyze these applications in secure environments.
Are there safe alternatives to iofbodies.com tools
Yes. Open-source tools like Kali Linux, Burp Suite, and Metasploit offer verified and secure testing options.
How can users test iofbodies.com tools safely
Use virtual machines, sandbox environments, or isolated hardware to test these tools without endangering live systems.





